Hei! 10+ Sannheter du Ikke Visste om 800 30 Risk Assessment Spreadsheet? Join ingram micro cyber security as we delve into.
800 30 Risk Assessment Spreadsheet | Guide to using a risk register example included projectmanager com / our free risk assessment spreadsheet provides a basic starting point for risk assessments. An effective risk management program. Risk determination risks and associated risk levels step 8. Control recommendations recommended controls step 9. Determine the likelihood of threat.
An effective risk management program. Guide to using a risk register example included projectmanager com / our free risk assessment spreadsheet provides a basic starting point for risk assessments. A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business. Has been added to your cart. With a detailed and complete document of information security risk assessment.
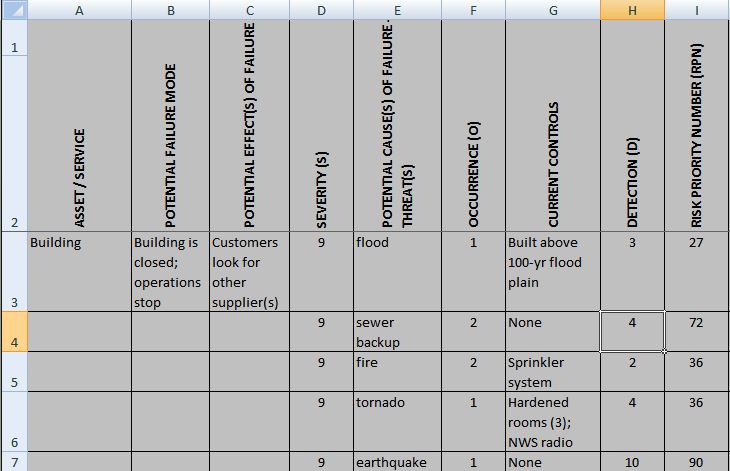
There are many techniques used to carry out information security risk assessments. With a detailed and complete document of information security risk assessment. The risk assessment methodology covers following nine major steps. Why is risk assessment important? Um, how do we continue to monitor what we've assessed today. Risk management is a practical step in handling risk scenarios in an organization, including in the field of information security. Each risk might be ranked with adjectives such as low, medium, or severe. Join ingram micro cyber security as we delve into. Determine the likelihood of threat. Then assessing, responding and monitoring. 800 30 risk assessment spreadsheet : The risk assessment process includes the following steps: Control recommendations recommended controls step 9.
Assess current security measures 5. Um, how do we continue to monitor what we've assessed today. Why is risk assessment important? Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an. Each risk might be ranked with adjectives such as low, medium, or severe.

Determine the likelihood of threat. There are many techniques used to carry out information security risk assessments. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an. Why is risk assessment important? Identify the scope of the analysis 2. Dash 30 is what focuses in on the assessment piece and is gonna provide us with a very specific methodology what are the processes of risk assessments? Join ingram micro cyber security as we delve into. Risk assessment template excel spreadsheet spreadsheettemple risk assessment excel template. Then assessing, responding and monitoring. Risk management is a practical step in handling risk scenarios in an organization, including in the field of information security. This is a limited and watermarked version of our task based risk assessment. Our free risk assessment spreadsheet provides a basic starting point for risk assessments. An effective risk management program.
The risk assessment methodology covers following nine major steps. Join ingram micro cyber security as we delve into. Then assessing, responding and monitoring. Control recommendations recommended controls step 9. Guide for conducting risk assessments joint task force transformation initiative.

There are many techniques used to carry out information security risk assessments. Determine the likelihood of threat. Learn vocabulary, terms and more with flashcards, games and other study tools. Risk assessment process identifikasi risiko mengenali peristiwa yang mungkin dapat terjadi dan berakibat negatif. 800 30 risk assessment spreadsheet : Prepare for assessment by identifying scope 2. With a detailed and complete document of information security risk assessment. Guide for conducting risk assessments joint task force transformation initiative. Um, how do we continue to monitor what we've assessed today. Risk management is a practical step in handling risk scenarios in an organization, including in the field of information security. Identify the scope of the analysis 2. This is a limited and watermarked version of our task based risk assessment. Risk assessment template excel spreadsheet spreadsheettemple risk assessment excel template.
800 30 Risk Assessment Spreadsheet: A risk assessment identifies and catalogs all the potential risks to your organization's ability to do business.
0 Response to "Hei! 10+ Sannheter du Ikke Visste om 800 30 Risk Assessment Spreadsheet? Join ingram micro cyber security as we delve into."
Post a Comment